CompTIA A+ Core 2: Practice Tests
CompTIA A+ Core 2 Practice Test 4
Continue your test prep with our fourth CompTIA A+ Practice Test 1202. These tests provide a fast, effective way to gauge how well you understand the key topics on the Core 2 exam. Use this free set of questions to review essential concepts and reinforce the skills you’ll need.
Time limit: 0
Quiz Summary
0 of 20 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Test complete. Results are being recorded.
Results
0 of 20 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Question 1 of 20
1. Question
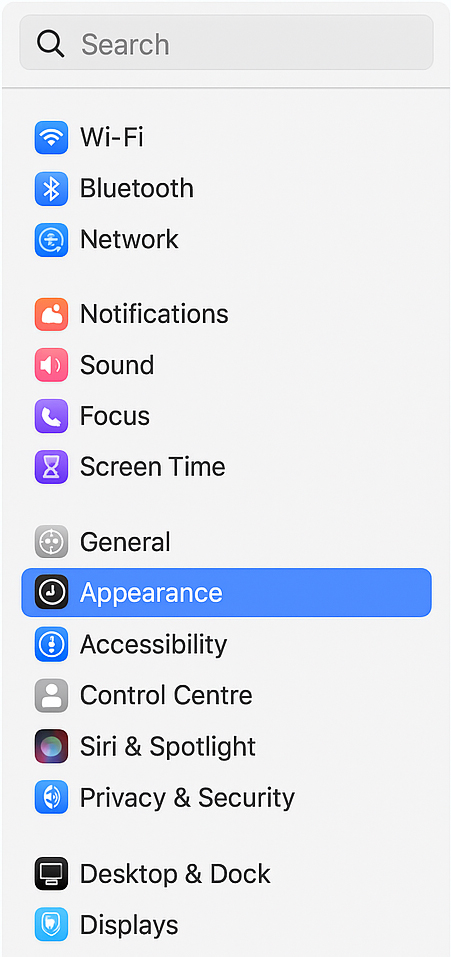
You want to hide the battery percentage displayed on the menu bar of macOS Sonoma 14. Which category in the system settings can turn off the battery percentage? (Refer to the exhibit.)
 CorrectIncorrect
CorrectIncorrect -
Question 2 of 20
2. Question
Jane is using an app that was developed by her company for internal use. She runs the app on her MacBook Air (13-inch, mid-2021). The app quits unexpectedly without displaying any error messages. The other apps on her machine work without any problem. She wants to help her development group isolate the issue. Which troubleshooting tools or techniques would you advise to isolate the issue best?
CorrectIncorrect -
Question 3 of 20
3. Question
Which process in macOS lists applications that store documents and data in iCloud?
CorrectIncorrect -
Question 4 of 20
4. Question
Josh wants you to update all the apps on an Ubuntu system. Which single command can update all the apps on Ubuntu Linux?
CorrectIncorrect -
Question 5 of 20
5. Question
Your colleague executes the command “chmod 664 abc.doc” and then runs “cp *.doc myfilesonly”. What do these commands accomplish? (Choose two.)
CorrectIncorrect -
Question 6 of 20
6. Question
You want to back up a few important documents and images on your Ubuntu system, but you do not want to use the rsync command. Which GUI application can you use to ease up the backup process?
CorrectIncorrect -
Question 7 of 20
7. Question
Which system implementation allows a Linux system to communicate and share files with a Windows system?
CorrectIncorrect -
Question 8 of 20
8. Question
You are using Red Hat Enterprise Linux 8 and want to update an existing software package. Which commands check for and install software updates? (Choose two.)
CorrectIncorrect -
Question 9 of 20
9. Question
The security department wants to monitor the backdoors that people do not use to enter the premises. Which motion sensor is suitable for detecting heat signatures?
CorrectIncorrect -
Question 10 of 20
10. Question
Which biometric technology is the hardest to break into and is only installed at the entrance to highly sensitive areas?
CorrectIncorrect -
Question 11 of 20
11. Question
Your organization requires all employees to have access to only the resources that are absolutely necessary for their jobs. It means that a database administrator will have access to the database servers only. Which principle is being implemented in this scenario?
CorrectIncorrect -
Question 12 of 20
12. Question
You want to restrict the domain users in your department from accessing the command prompt and installing any software on their Windows systems. Which Windows Active Directory feature can help you accomplish this task?
CorrectIncorrect -
Question 13 of 20
13. Question
You are testing automated door locks that utilize IoT (Internet of Things) technology. Which Wi-Fi protocol is considered the safest for such devices?
CorrectIncorrect -
Question 14 of 20
14. Question
AES symmetrical keys with 256 bits can produce ____________ possible keys. (Fill in the blank.)
CorrectIncorrect -
Question 15 of 20
15. Question
Whenever you log into the company servers, you must type your username and password first and then type an OTP (one-time password) sent to your mobile device. What type of authentication does this refer to?
CorrectIncorrect -
Question 16 of 20
16. Question
Which security threats are most commonly delivered via email? (Choose two.)
CorrectIncorrect -
Question 17 of 20
17. Question
Which of the following attack vectors causes frequent browser redirections on a Windows system?
CorrectIncorrect -
Question 18 of 20
18. Question
How does polymorphic malware evade detection on a Windows system?
CorrectIncorrect -
Question 19 of 20
19. Question
You want to prevent a local application from reaching a specific website due to security concerns. Which of the following methods can achieve this objective? (Select two.)
CorrectIncorrect -
Question 20 of 20
20. Question
Security personnel often use mantraps and turnstiles to prevent which of the following security threats?
CorrectIncorrect
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- Current
- Correct
- Incorrect
