Network+ Practice Tests
CompTIA Network+ Practice Test 7
Complete your Network+ preparation with our final practice test containing 30 more exam-simulation questions. Every question features comprehensive explanations to solidify your understanding of key networking concepts.
Quiz Summary
0 of 30 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 30 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
-
Question 1 of 30
1. Question
You’re configuring a wired home network with four Windows computers, a switch, and a cable router that provides Internet access. All the computers can access the Internet, but none can access filesystem shares on each other. What is the most likely cause of the problem on the four network computers?
CorrectIncorrect -
Question 2 of 30
2. Question
You are configuring a content filtering policy for images and text on a specific website. Which rules can be configured to filter content according to administrator-set policies?
CorrectIncorrect -
Question 3 of 30
3. Question
Why is it NOT advisable to put a subnet outside firewalls when configuring publicly viewable servers, such as web, FTP, and email relay?
CorrectIncorrect -
Question 4 of 30
4. Question
You are gathering information about an incident that left many users unable to access the company’s intranet. What type of questions should you ask when gathering information about the incident that might help you identify the problem?
CorrectIncorrect -
Question 5 of 30
5. Question
You get a call from one of the salespeople. He said he could get to the Internet but not the sales server, and that he is about to lose a huge sale. Which of the following is the most likely cause of the problem?
CorrectIncorrect -
Question 6 of 30
6. Question
A significant network problem occurred, with the web servers shutting down. John and his team are on the clock, trying desperately to identify the problem. He starts at the Physical layer, checks everything, and moves to the OSI model’s top layers. Which approach is being employed in this scenario?
CorrectIncorrect -
Question 7 of 30
7. Question
You are troubleshooting a DNS problem in the network. After establishing and testing a theory of probable cause, you discover that the theory was not the cause of the issue. You tried and exhausted all theories, but the problem remained. What is the next logical step according to the CompTIA troubleshooting methodology?
CorrectIncorrect -
Question 8 of 30
8. Question
At which step of the troubleshooting methodology have you devised a solution to a DNS problem and begun implementing it on the end-user device while awaiting results?
CorrectIncorrect -
Question 9 of 30
9. Question
You are troubleshooting misconfigured routes on one of the routers. Which troubleshooting step saves a lot of time by narrowing the problem to a missing route?
CorrectIncorrect -
Question 10 of 30
10. Question
You are troubleshooting a switch that has three computers connected to it. However, only two can communicate with each other. After confirming that the hardware is functioning properly, which of the following probable causes can be singled out for the third computer’s communication problem?
CorrectIncorrect -
Question 11 of 30
11. Question
What kind of issue can occur when an electromagnetic signal conducted on copper wires is in close proximity to another cable?
CorrectIncorrect -
Question 12 of 30
12. Question
You want a cabled connection between two switches. To avoid TX/RX transposition, which of the following cable pin layouts should you use?
CorrectIncorrect -
Question 13 of 30
13. Question
Which network interface occurrences cause malfunctions on a full-duplex Ethernet network? (Choose two.)
CorrectIncorrect -
Question 14 of 30
14. Question
You have received reports that some employees are staying late in the office, using office resources to play networked computer games with each other after hours. After investigating the MAC address table on the main network switch, you suspect someone is connecting an unauthorized switch to the main switch’s Ethernet port. Which command should you use to secure and prevent employees from connecting external switches to the network?
CorrectIncorrect -
Question 15 of 30
15. Question
Which Power over Ethernet (POE) standard delivers more power and is compatible with Gigabit Ethernet with four wire pairs at 25.5 watts?
CorrectIncorrect -
Question 16 of 30
16. Question
Which five states can the ports on a bridge or switch running Spanning Tree Protocol (STP) transition through?
CorrectIncorrect -
Question 17 of 30
17. Question
A network administrator is configuring default routes. What is the network destination address for the host system’s default route in an IPv4 routing table?
CorrectIncorrect -
Question 18 of 30
18. Question
The DHCP server on your local network has stopped assigning IP addresses to new systems. Upon investigation, you discover that the DHCP server’s IP address scope is exhausted. What should you do to address this issue quickly?
CorrectIncorrect -
Question 19 of 30
19. Question
Jane has been assigned to build a domain controller for a new branch office. After installing a new Windows server and configuring it as a domain controller, she connects it to the office network. However, the domain controller fails to synchronize with the existing systems at the office. Which of the following could be the cause of this problem?
CorrectIncorrect -
Question 20 of 30
20. Question
A corporate network user cannot access the Internet or communicate with devices outside their local subnet. They can, however, successfully connect to internal resources on the same subnet. Upon troubleshooting, you notice the following configuration:
IP Address: 192.168.1.25
Subnet Mask: 255.255.255.0
Default Gateway: 192.168.2.1What is the most likely cause of this connectivity issue?
CorrectIncorrect -
Question 21 of 30
21. Question
A new folder has been uploaded to the company’s intranet servers. It contains training videos larger than 1GB. The marketing and sales teams were encouraged to access it at 8 AM and participate in the training session. The server hosting the files is an old system with limited resources. At 8:05 AM, the network slows down, and many users complain about not seeing the resource on the network. Many have their video streams stuck. Which network component is the most likely cause of this problem?
CorrectIncorrect -
Question 22 of 30
22. Question
When data packets are transmitted over a network, an external disturbance might cause temporary service interruptions, dropouts, or even data loss. Which term describes this external disturbance?
CorrectIncorrect -
Question 23 of 30
23. Question
You are downloading a large file from the Internet, and midway through, the download speed drastically slows down, resulting in a longer-than-expected download time. The Internet connection is stable and provides good download speeds. Which of the following is most likely the cause of this slowdown?
CorrectIncorrect -
Question 24 of 30
24. Question
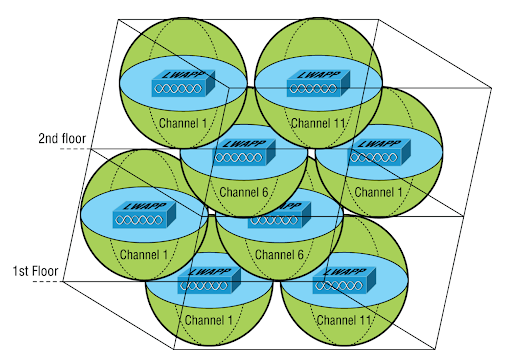
Your company has multiple floors in a building, each with multiple WLANs. You want to configure the channel usage three-dimensionally, ensuring no channel overlap. Which hardware should be used to prevent bleed from one floor to another?
CorrectIncorrect -
Question 25 of 30
25. Question
Which of the following is NOT one of the legitimate causes of roaming misconfiguration?
CorrectIncorrect -
Question 26 of 30
26. Question
A network administrator suspects someone in the office uses a Microsoft tablet to connect to the network. Any external devices are explicitly prohibited in the office. Assuming that the office network is 192.168.10.0/24, which command can be used to find illegal devices by discovering all the live hosts on the network?
CorrectIncorrect -
Question 27 of 30
27. Question
You are working with Cisco routers for a client with an office spanning multiple floors in a building. While configuring the switch attached to a Cisco router, you thought about finding the devices connected directly to the router. You access the Bash shell and use the show cdp neighbors command. Which protocol was used in the command?
CorrectIncorrect -
Question 28 of 30
28. Question
A visual fault locator cable continuity test can do all of the following except:
CorrectIncorrect -
Question 29 of 30
29. Question
Which of the following commands displays the output in the exhibit?
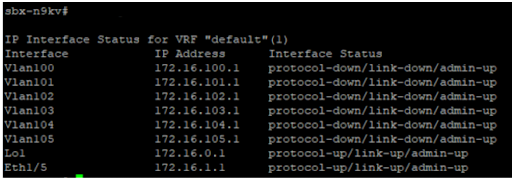 CorrectIncorrect
CorrectIncorrect -
Question 30 of 30
30. Question
You are configuring a port to belong to a VLAN by assigning a membership mode. After the assignment, you execute the ‘show vlan’ command. Next, you want to configure multiple ports at the same time. Which command is most appropriate for this task?
CorrectIncorrect
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
- 30
- Current
- Correct
- Incorrect
